Technology Insights into Vaccine SPAM and Bad Actors
At Altamente we are tasked with managing a wide range of client communications and web infrastructure, which encompasses areas such as email, web, and messaging systems. With over two decades of experience in this field, we have a unique understanding of the cyclical nature of threats, attempted breaches, phishing efforts, and various forms of spam.
Observations suggest a significant effort is currently being deployed with the intention of undermining public trust in government, public health, and societal institutions. This report serves to highlight an instance of such attempts, demonstrating the recent trend of misinformation.
Recent misinformation campaigns have shown a concentrated focus on vaccination efforts, attempting to foster mistrust towards the medical community and governing bodies. The following illustration presents a portion of a spam comment aimed at promoting a common conspiracy theory related to the Covid-19 vaccines, namely, the myth of "vaccine shedding".
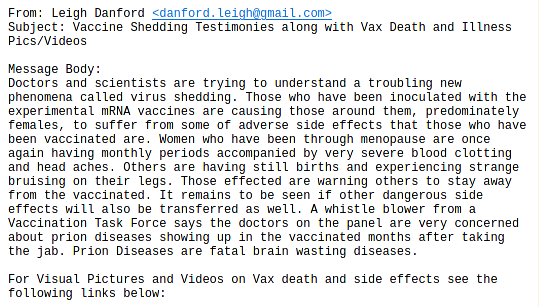
For a factual overview of "vaccine shedding", please refer to the related Wikipedia article. The concept of "virus shedding" is not a concern associated with modern vaccines, and these efforts aim to generate confusion by referring to outdated practices from the 1950s.
These concerted disinformation efforts, which involve significant time and resources, often raise questions about the motivations behind such campaigns. Why is there such commitment to disseminating spam and misinformation? This question brings us to the intersection of technology and human action.
The Interplay Between Technology and Human Activity
An in-depth analysis of these campaigns reveals that the individuals or organizations behind these attempts are not merely concerned citizens expressing their views. They are often employed to propagate this misinformation. A review of our server logs indicates that a substantial amount of the traffic to our hosted websites originates from regions such as China, Russia, Ukraine, and Belarus. Given that the content we host holds little relevance for individuals in these regions, it becomes evident that the primary motive is exploitation of WordPress's popularity for disruptive and potentially harmful purposes.
This scenario necessitates the implementation of measures like captchas, designed to filter out automated spam posts. However, it's important to remember that human beings are sometimes paid to execute these tasks, illustrating that these campaigns are indeed orchestrated efforts.
To those who may find these posts credible, it's crucial to understand that these operators are not acting in your interest. They are manipulating public sentiment to achieve their own goals, often at the expense of national unity, faith in public institutions, and scientific discourse. The resultant divisions and societal disruption serve their objectives, often to the detriment of political and economic stability.